The Video Security market is at an inflection point. Technological advances have replaced legacy approaches with modern security systems that integrate hardware and software or equip existing cameras with modern cloud and computer vision capabilities. After getting off the ground in the last 5-10 years, next-generation players have started to gain meaningful traction in the market, which boasts a market size of at least $10B within the US alone.
Simultaneously, the nascent category of Video Intelligence is starting to emerge. Video Intelligence builds on the success of using video data for physical security and public safety by developing tailor-made software and insights for other use cases, such as workforce management, customer experience, store performance, sports analytics, etc. As the Video Intelligence category matures, every professional will eventually be able to access insights and analytics from video data to support day-to-day objectives.
In this post, we break down how the Video Security and Video Intelligence categories have evolved to date, where both are headed next and what it will take for vendors to build dominant businesses in each category.
Video Security’s Netflix Moment
Prior to 2010, video security systems consisted of cameras connected to an on-premises recording and storage device, such as a digital video recorder (DVR) or network video recorder (NVR). We refer to this as Phase 1 of video security system architecture.
Expand
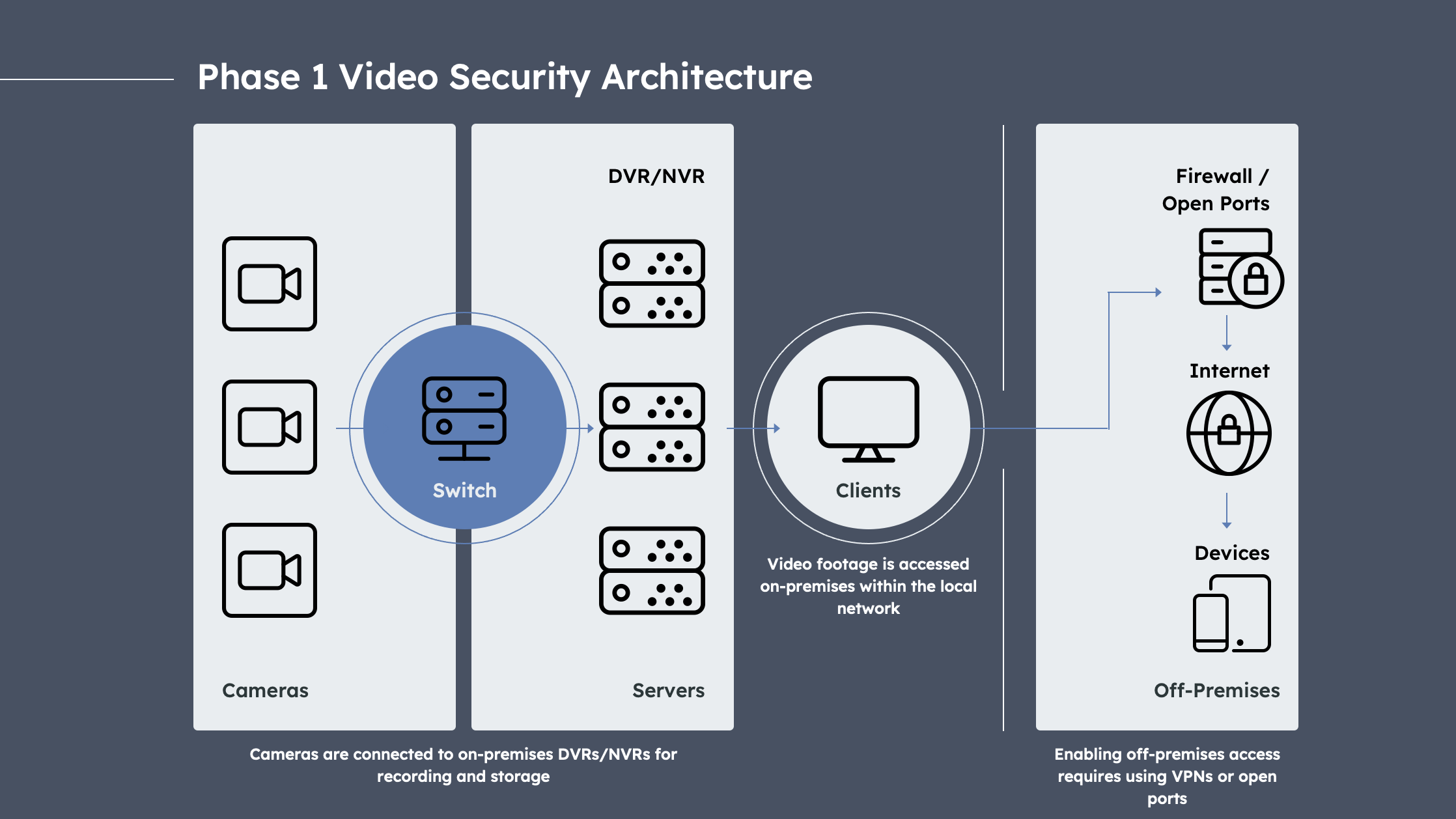
Phase 1 Video Security Architecture: Adapted from Verkada
Phase 1 video security architecture had a number of challenges:
- Users had to be on-site or logged in remotely via VPN to access video footage, meanwhile other software applications had transitioned to the cloud.
- Increased workload for IT teams who are on the hook for maintaining hardware as well as managing firmware upgrades, patches, and fixes.
- Heightened cybersecurity risks due to failure to keep up with firmware upgrades as well as insecure remote access practices such as poorly configured VPNs or open ports, using factory default settings and shared passwords etc.
- Scaling a security program or camera fleet built around on-premise DVRs/NVRs is not plug-and-play, as each DVR/NVR device can only support and store footage from a limited number of cameras.
- Centralizing storage of video data on an on-premise DVR/NVR represents a single point of failure, which introduces risk of losing footage if devices fail or are tampered with.
- Lack of active monitoring and proactive downtime alerts which makes it difficult for physical security teams to quickly address camera malfunctions.
In 2016, disrupters such as Verkada and Rhombus emerged with an alternative to the centralized DVR/NVR-based architecture. In what we call Phase 2 of Video Security, these companies developed an “edge-based” architecture, combining recording, storage and computer vision processing on cameras themselves, eliminating the need for DVRs/NVRs.
Expand
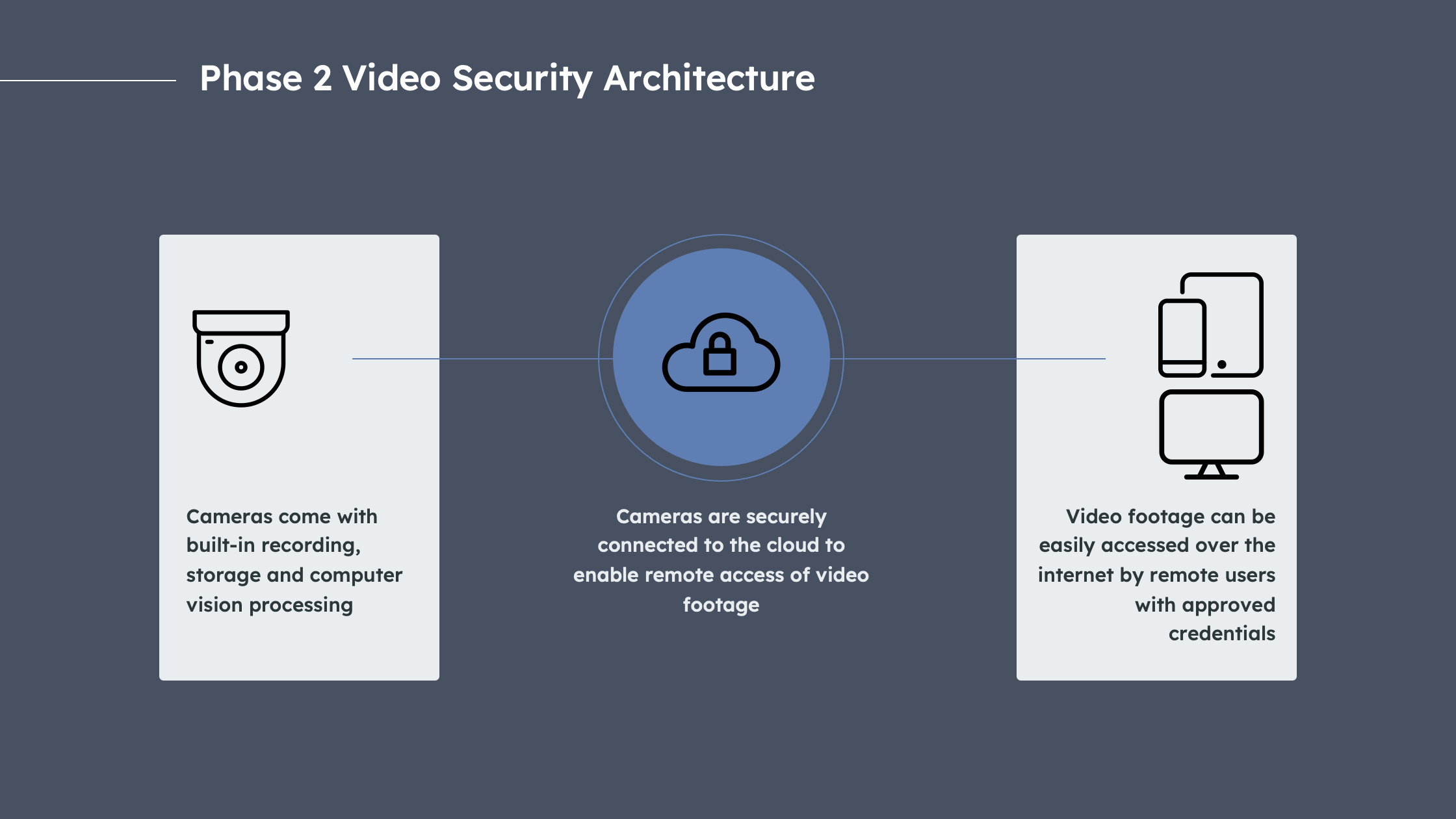
Phase 2 Video Security Architecture: Adapted from Verkada
Cameras are connected to the cloud, so with the right credentials, video footage can be accessed over the internet, similar to logging into a Netflix account. To the relief of IT teams, this also meant that software and cybersecurity updates would be continuously maintained by vendors. The edge-based approach also allowed customers to install additional cameras without concern for DVR/NVR capacity limits. In addition, decentralized recording, storage and processing on each camera combined with cloud storage backups eliminated the single point of failure issue that Phase 1 video security systems suffer from. Finally, Phase 2 video security systems proactively notify users when a camera is offline or malfunctioning.
Phase 2 vendors also introduced new and improved functionality such as the ability to:
- Tag and search for objects of interest in large volumes of video data
- Share video feed segments with external parties such as law enforcement and
- Use sophisticated computer vision that can tell the difference between a human intruder and a bird in a restricted zone for example
The edge-based architecture brought significant benefits but these improvements came at a cost that included purchasing proprietary cameras developed by Phase 2 vendors which can be an expensive undertaking, paying for installation services, upgrading broadband and other IT infrastructure and paying for ongoing access to software. For some buyers, this cost is simply too high to bear, and it is this pain point that gave rise to the next phase of Video Security.
In the mid-late 2010s, Phase 3 vendors emerged to address this problem. Phase 3 vendors developed an approach that enables buyers to keep their existing cameras, which run on Phase 1 DVR/NVR architecture, while gaining the benefits of the modern software and analytics pioneered by Phase 2 vendors. To do so, Phase 3 vendors access the video feed from existing cameras by installing a “Cloud NVR” or similar on-site device (edge-to-cloud bridges, edge servers, etc.).
Expand
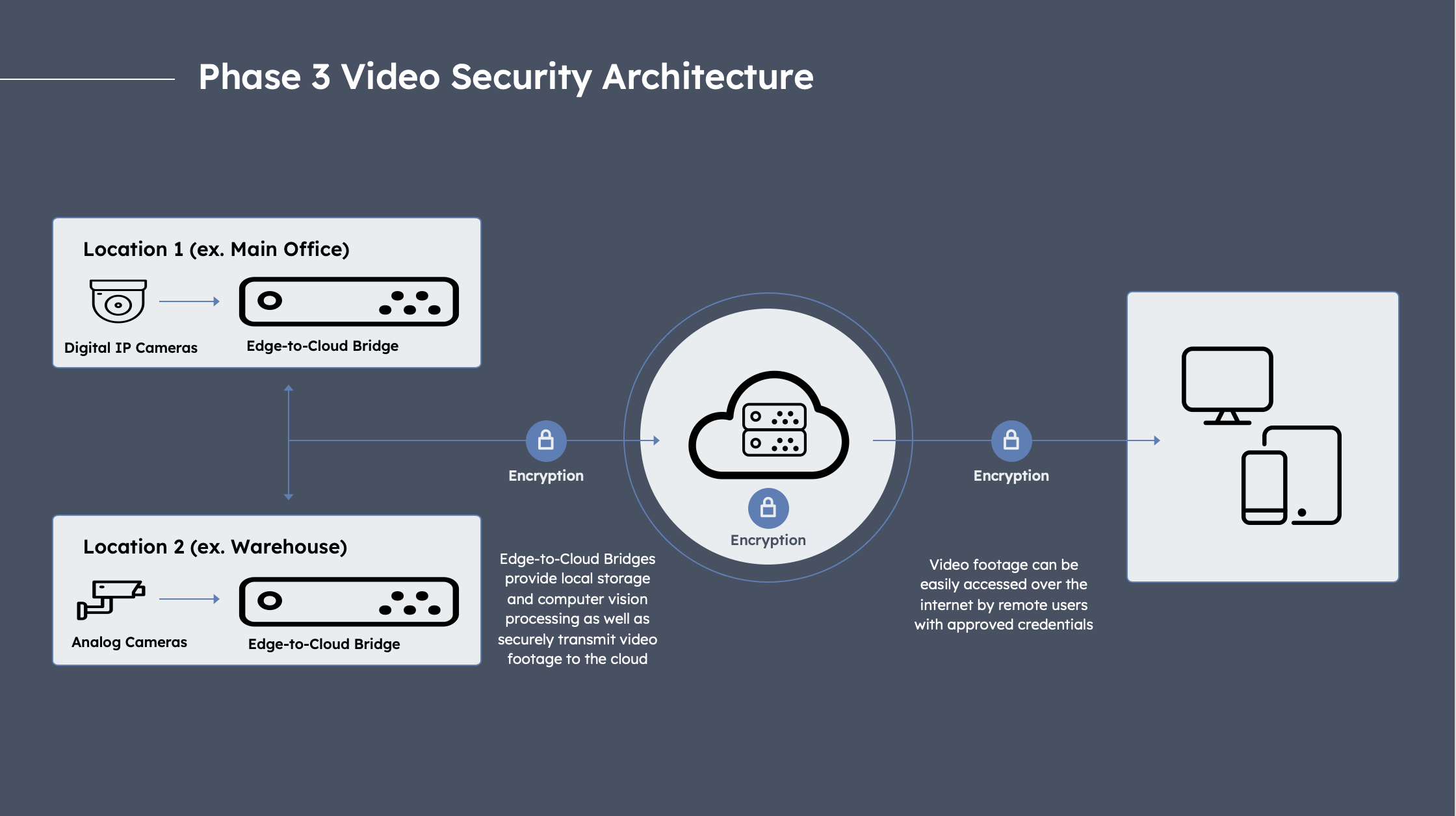
Phase 3 Video Security Architecture: Adapted from Eagle Eye
Cloud NVRs are similar to traditional DVRs/NVRs but are connected to the internet and can store video data both locally and in the cloud. Cloud NVRs provide many of the benefits that Phase 2 vendors offer, including advanced software and analytics capabilities. However, as with any device, this comes with the trade-off of requiring physical space for the Cloud NVR hardware, Cloud NVRs only support a limited number of cameras and so scaling requires additional devices, single point of failure risk if the Cloud-NVR device is compromised etc.
Some Phase 3 vendors also link to existing cameras without an intermediary device by connecting to the customer’s local network and accessing video feeds using industry protocols such as ONVIF and RTSP.
Why We’re Excited About Video Security
Keeping people, property and equipment secure is fundamental to running a business, so it’s no surprise that virtually every industry has adopted Video Security in some form. We believe the Video Security market represents an attractive investment opportunity for the following reasons:
- Large Market: Video Security is estimated to be a $10B+ market in the US alone with buyers constantly upgrading their camera hardware and software to take advantage of the latest technology. The market size, industry replacement cycle and impressive execution has driven strong growth at scale in companies like Verkada, Flock Safety and LiveView Technologies (LVT).
- Resilient Demand: Video Security has seemed almost impervious to recent softness in the economy, which reflects the fact that security is a budgetary imperative and benefits from a natural refresh cycle where legacy video security systems reach their end of life and need to be replaced. Video Security also benefits from broad-based demand, including from the education sector thanks in part to government grants for school safety
- Expansion into Physical Security: For many vendors, Video Security serves as a starting point to developing an end-to-end physical security platform that also offers solutions for access control, alarms, visitor management etc. The evolving messaging of Phase 2 vendors illustrates this clearly: both Verkada and Rhombus started out with slogans like “No NVR or DVR Required” and “Ditch the NVR”. As they matured into full-fledged physical security platforms, their taglines then changed to “Simplify Physical Security at Scale” and “The New Standard in Physical Security”.
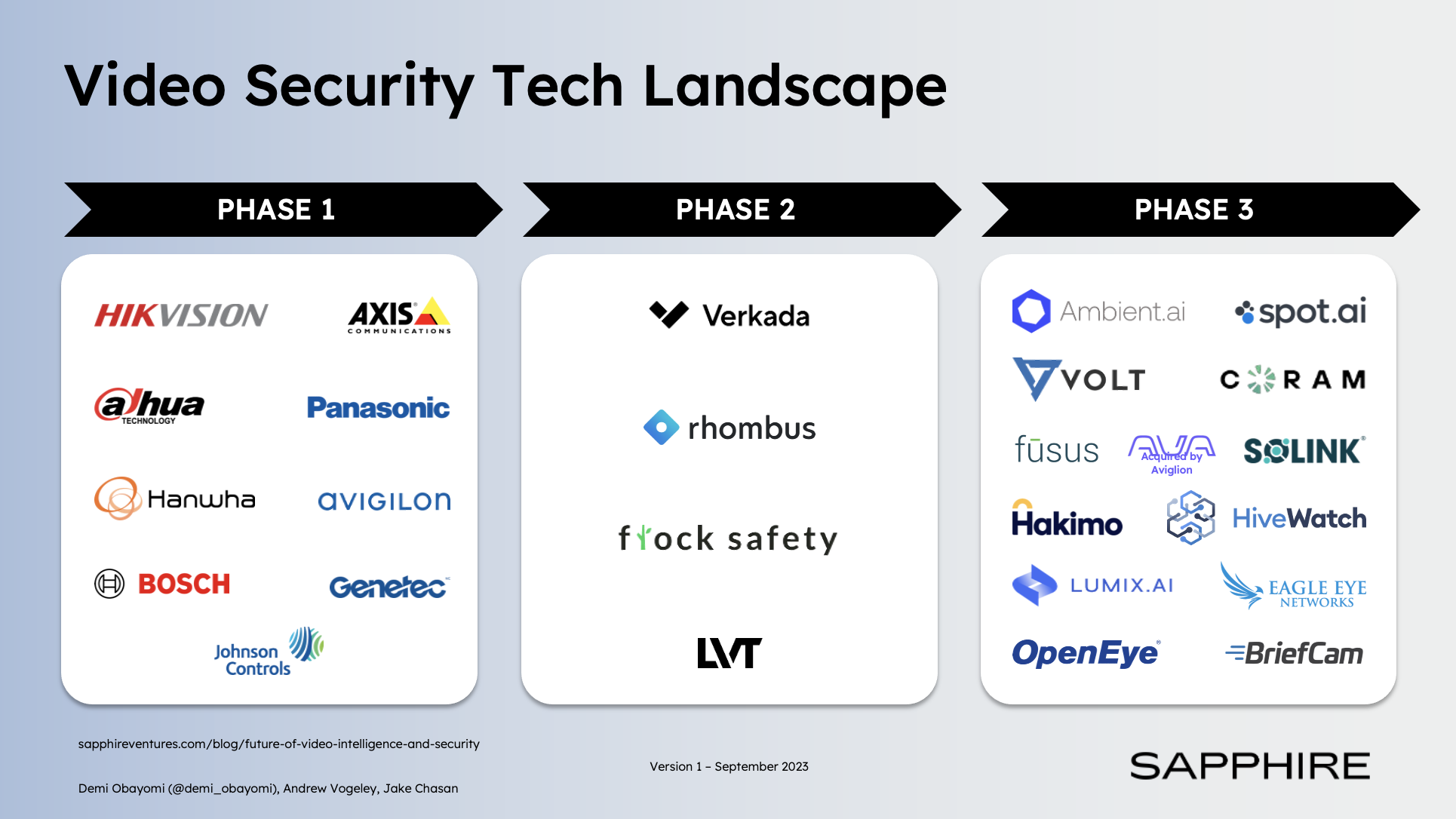
Below we present a representative market map of Video Security vendors categorized based on our assessment of the phase of the market in which each vendor originally emerged (NB: many vendors have or are in the process of shifting right to support Phase 2 or Phase 3 architectures). It is our view that Phase 2 and Phase 3 vendors represent the future of the market and in the next section we discuss which of these two categories of Video Security vendors is best positioned to win the Video Security streaming wars.
Who Will Win the Video Security Streaming Wars?
Both Phase 2 (edge-based architecture) and Phase 3 (Cloud NVR architecture) Video Security vendors offer similar advanced software and analytics functionality. The key difference is that a typical Phase 2 vendor will require its customers to replace their existing cameras with the vendor’s proprietary cameras, while Phase 3 vendors are hardware-agnostic and support any camera at all. It remains to be seen whether companies that tightly integrate hardware and software (Phase 2) or those that decouple them (Phase 3) will dominate the Video Security category and in our discussions with vendors and industry experts, there is no clear consensus either as there are merits to both approaches.
Buyers with dated or failing cameras are likely to replace them, which neutralizes a key selling point for Phase 3 vendors (though some Phase 3 vendors offer free cameras) and plays into the hands of Phase 2 vendors. In addition, Phase 2 vendors are more established than Phase 3 vendors and have the channel partner relationships in place to compete for more new business opportunities.
However, there are buyers that already have working cameras in place. Some buyers also have a preferred camera vendor that they have a longstanding relationship with. Finally, other buyers are unwilling to consider the outlay required to remove their existing cameras and then purchase and install Phase 2 vendors’ (often expensive) proprietary cameras due to budget constraints or the sheer size of their existing camera fleet. Such buyers are likely to gravitate toward the camera-agnostic approach of Phase 3 vendors.
We expect both Phase 2 and Phase 3 approaches to command sizable market share and predict that the Video Security wars between Phase 2 and Phase 3 vendors will not result in a winner-take-all end state. However, there is one caveat to our prediction given that most video security systems are purchased through channel partners who effectively serve as gatekeepers in the industry.
Regardless of whether a vendor takes the Phase 2 or Phase 3 approach, we believe the most successful companies will be those that successfully convince channel partners to carry their products. Most buyers purchase video security solutions through AV or security system integrators due to the value-added services such as consulting, installation and configuration, needed to select the right video security system and get it up and running on-site. Channel partners typically only work with a small number of vendors and are very selective in adding new vendors to their lineup. This dynamic can be an obstacle to new vendors seeking to break into the Video Security market. As a result, nailing the channel partner GTM strategy will be key for any vendor pursuing the Video Security market regardless of architectural approach.
Is the Success of Video Security A Sneak Preview of What’s to Come?
Video Security is an established and well-known category. Our research shows that using video for security purposes, while popular and effective, is only one use case under the umbrella of Video Intelligence. Nearly every industry can benefit from tailored Video Intelligence use cases:
- Food and beverage manufacturers use video to improve workplace safety by detecting hazards and accidents and by identifying unsafe behavior
- Theme and amusement parks use video to improve customer experience by tracking live wait times and measuring throughput of each ride or experience
- Restaurants use video for workforce management, such as tracking time and attendance and optimizing staffing based on occupancy trends
- Retailers use video to optimize store performance by analyzing brand and product placement as well as the success of promotions and campaigns using heatmaps
- Auto service providers, such as car washes, use video for tracking operations metrics such as vehicle throughput, capture rate and client retention rate
- Commercial real estate firms use video to automate parking lot management through license plate recognition
These are just a few of the examples we’ve seen and we fully expect many more use cases to emerge as the Video Intelligence category gains steam.
Why We’re Excited About Video Intelligence
Cameras are all around us – in office buildings, restaurants, airports, train stations, parking garages and more. The global number of surveillance cameras is estimated to be as high as 1B. These cameras are always on, generating hundreds of petabytes of data. Historically, this trove of video data has primarily been used for physical security and public safety. Now, many more use cases are emerging across all industries.
Insights from context-rich video data can be useful to teams across the business. Organizations at the cutting edge combine video intelligence with data from other systems (e.g., POS, ERP) to optimize operations, streamline processes and improve customer experience. This trend is rapidly leading to the growth of a Video Intelligence category that we believe is appealing for the following reasons:
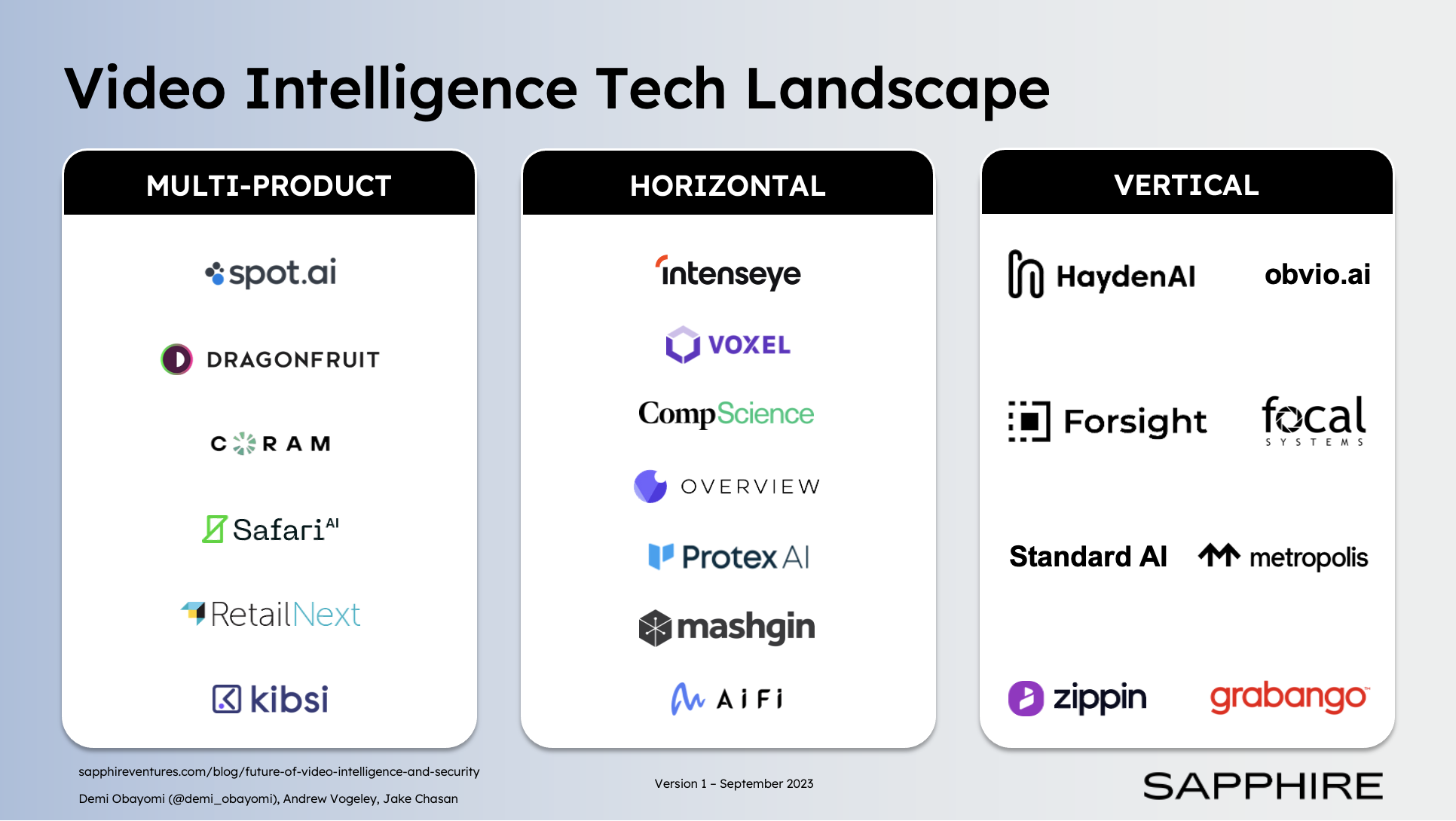
- Endless Use Cases Point to Substantial Market Size: Video intelligence use cases are nearly unlimited. In addition to the examples mentioned earlier, manufacturers are using video to monitor production lines, pharmacies are using it to verify prescription fulfillment, retailers are disputing fraudulent chargebacks with video evidence tied to POS data, transportation authorities are automating tickets etc. We expect multiple large Video Intelligence businesses to emerge in the coming years with a variety of business models, including:
- Multi-product: Selling an assortment of use cases into a wide range of verticals.
- Horizontal: Selling a specialized use case into a wide range of verticals.
- Vertical: Addressing one or multiple use cases within a specific industry.
- Unlocks Opportunities for Significant Automation: If you’ve ever visited an Amazon Go store, you’ve experienced Video Intelligence to its fullest extent. Each store is jam-packed with hundreds of cameras that power a “walk in and walk out” customer experience. Outside of grocery and retail, checkout-free experiences are starting to emerge in categories such as parking. Grocery and retail stores are also using video intelligence to improve operations and profitability through real-time inventory updates, optimized store planograms and automated ordering.
- Greenfield Market Dynamics: Unlike the Video Security market, where incumbents have been in place for at least 20 years, many Video Intelligence use cases are greenfield in the sense that there is no existing vendor in place. Video Intelligence software often replaces manual work that humans tend to do inconsistently and inaccurately, such as physical inventory counts, worksite safety patrols and throughput measurement. With Video Intelligence, users are guaranteed always-on coverage as well as real-time insights and recommendations that allow them to fine-tune operations and reallocate labor capacity to higher-level tasks that impact business performance. While the greenfield nature of many Video Intelligence use cases is attractive, building a successful business will require effective category creation and market education.
We’re excited to see how the Video Intelligence category evolves. Below we present an illustrative market map of Video Intelligence vendors grouped by business model:
Building a Video Security or Video Intelligence Company? Get in Touch.
Video Security and Video Intelligence are highly dynamic categories. New approaches and use cases are constantly emerging, as vendors seek to gain the upper hand and meet insatiable buyer demand. At Sapphire, we’re keen to back companies bringing advanced software and analytics capabilities to the Video Security and Video Intelligence markets as part of our $1B commitment to invest in the next generation of AI-powered B2B and Enterprise tech startups.
Please reach out to Demi ([email protected]), Andrew ([email protected]) and Jake ([email protected]) if you are building a Video Security or Video Intelligence company. We can’t wait to hear from you!
Legal disclaimer
Disclaimer: Nothing presented within this article is intended to constitute investment advice, and under no circumstances should any information provided herein be used or considered as an offer to sell or a solicitation of an offer to buy an interest in any investment fund managed by Sapphire Ventures, LLC (“Sapphire”). Information provided reflects Sapphires’ views as of a time, whereby such views are subject to change at any point and Sapphire shall not be obligated to provide notice of any change. No assumptions should be made that investments described were or will be profitable. Due to various risks and uncertainties, actual events, results or the actual experience may differ materially from those reflected or contemplated in these statements. Nothing contained in this article may be relied upon as a guarantee or assurance as to the future success of any particular company. Past performance is not indicative of future results.