With an uncertain macroeconomic environment and mounting geopolitical tensions, calling the past few years tumultuous would be an understatement. Despite constant change, two things stayed consistent: cybercriminals remained unrelenting in their attacks, and cybersecurity held fast as a non-negotiable priority for organizations worldwide.
Software supply chain and ransomware attacks have more recently stepped into the limelight given the severity of their magnitude. REvil’s ransomware attack through Kaseya impacted 1,500 companies in minutes, the malware-ridden version of SolarWinds’ Orion software was installed by around 18,000 of their customers and the global-scale Log4j security vulnerability compromised libraries in 89% of IT environments.
In 2022, the onslaught of cyberattacks continued:
- The zero-day attack that exposed the data of more than 5 million Twitter accounts
- Two breaches of the password manager LastPass in three months
- The Lapsus$ group’s attacks on Okta, Uber, Rockstar, Nvidia and several other companies
- The data breach of Twilio from a phishing campaign by the 0ktapus group, which had downstream consequences for companies such as Doordash
- The breach of the source code in Okta’s Github repositories
It’s no surprise that IT leaders recognize there is little room to compromise on security. In fact, security software spend ranks as the least likely to be cut in an economic downturn according to Morgan Stanley’s latest CIO survey:
Expand
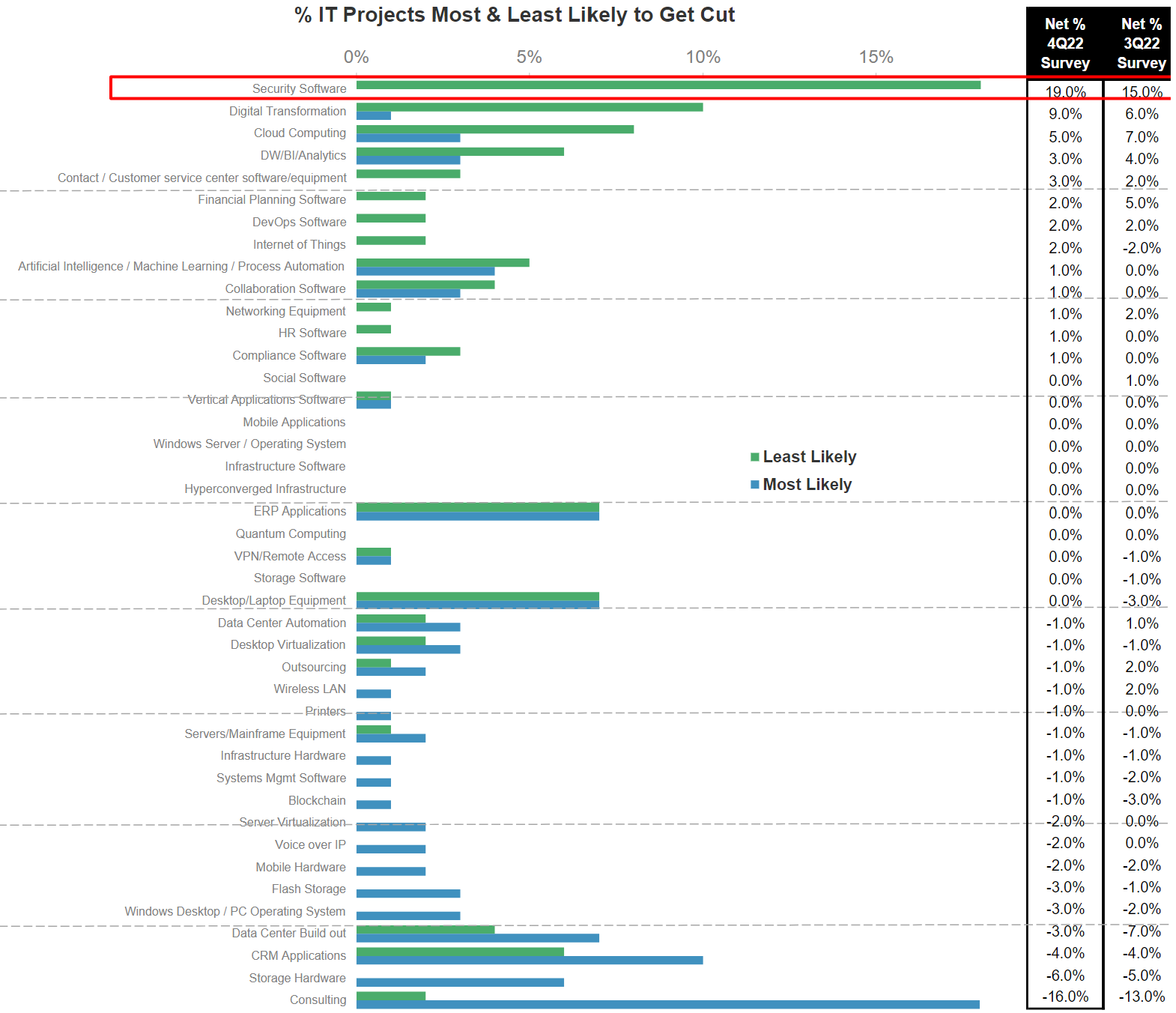
Source: Morgan Stanley, 4Q’22 CIO Survey
Cybersecurity Software Is Still In Its Early Innings
Cybersecurity is a unique industry — one with virtually no tolerance for errors and a constant feedback loop of innovation as defenders and attackers work diligently to outpace each other. We believe two major vectors keep the flywheel of cybersecurity innovation spinning:
- Expanding attack surfaces: The scope of security coverage has ballooned alongside the shift to cloud, containerization, remote work, SaaS app adoption, distributed systems, data sprawl — the list goes on. Each new system, network and application presents another entry point for adversaries to exploit; layering the human variable of properly managing and securing credentials further increases complexity.
- Breadth and depth of attacks: From solo hackers to cybercrime syndicates, threat actors are leveraging supply-chain vulnerabilities and automation to increase the scale of attacks (e.g., using botnets to perform DDoS attacks, credential stuffing, etc.) while being increasingly targeted when necessary (e.g., spear phishing, MFA fatigue, etc.). For instance, Akamai observed a peak of 25 million attempts per hour to exploit the Log4j vulnerability in December 2021.
These vectors help explain why, despite $179 billion being spent today on enterprise security globally, new breaches continue to be announced every week: a never-ending battle that has already propelled an immense amount of innovation across security technology and processes.
Despite this, we believe that security software is still in its early innings. $179 billion is just 4% of the $4.5 trillion that Gartner predicts will be spent on global IT this year. Of that $179 billion, 43% is spent on security services, down from 54% in 2018. While cybersecurity will always fundamentally require a combination of technology and people, much of security services spend is allocated toward ad-hoc, bespoke tasks that can and will be automated by software over time. As security becomes increasingly critical to business enablement rather than just compliance-driven, its share of total IT spend should also increase.
Expand
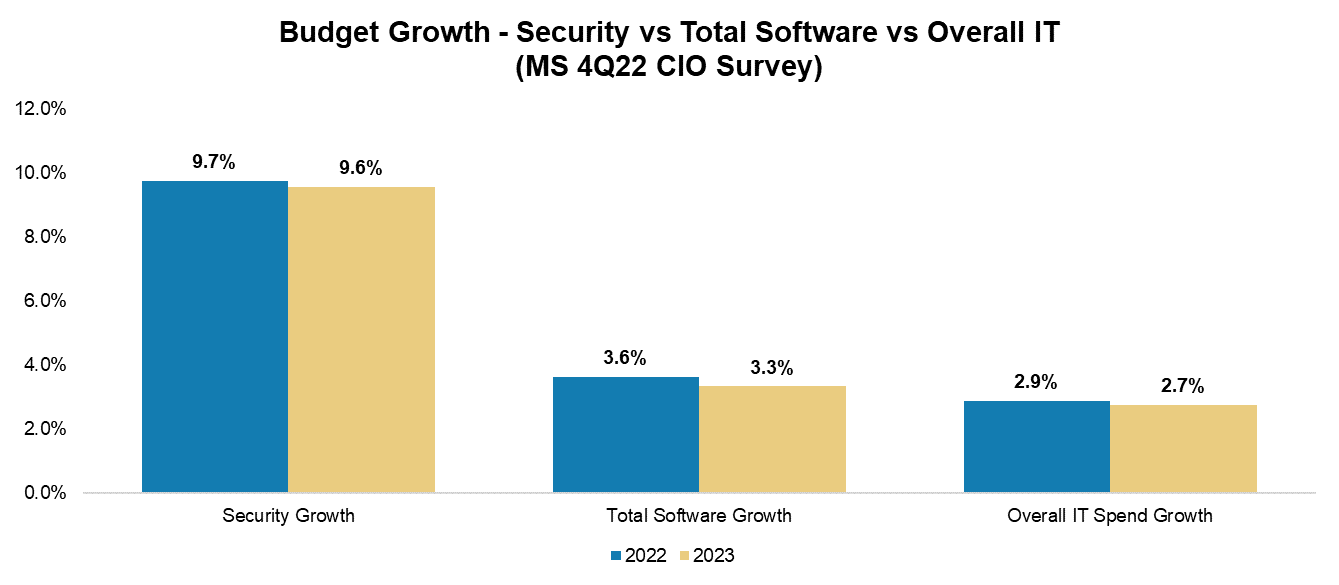
Source: Morgan Stanley, 4Q’22 CIO Survey
The Evolution of Security: How We Got To Now
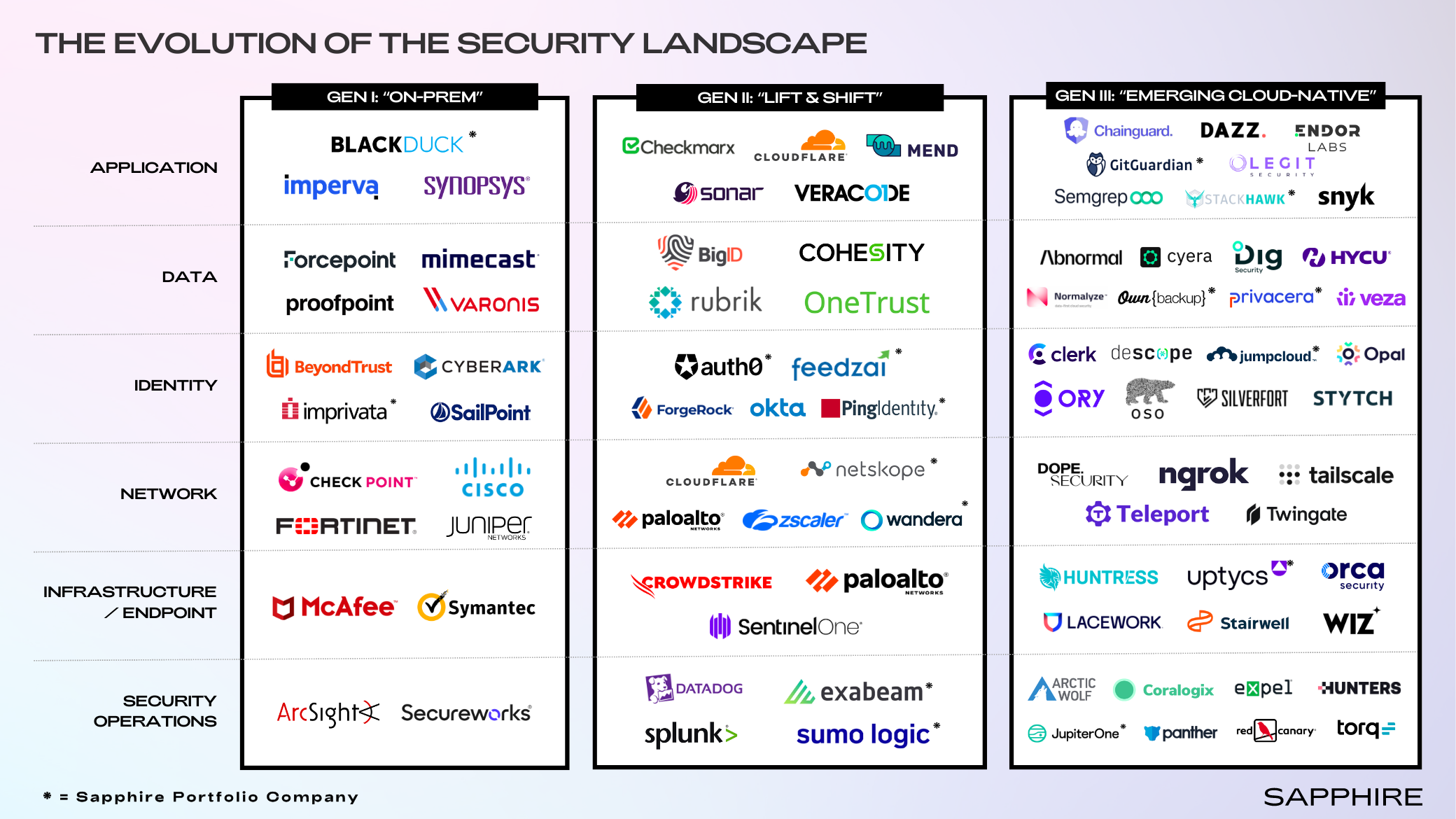
We primarily think of the security stack in terms of six major layers divided into two categories: assets (which include applications, data, identity, network, and infrastructure/endpoint) and security operations (which spans all assets).
In the coming months, we’ll delve deeper into each layer of the security stack, highlighting key trends and companies across each of these layers. Before that, we want to set the stage: how we got here and themes to keep an eye on as the security landscape further evolves.
Over the past three decades, security vendors have spanned three generations: the on-prem generation, “lift and shift” cloud solutions, and today’s emerging cloud-natives.
Generation I: “On-Prem”
The on-prem generation emphasized the “castle and moat” network security model, establishing an organization’s perimeter based on the assumption that relevant IT and data resided within its own walls and that threats needed to be blocked from outside.
However, the model’s key premises broke down over time. Assuming that anyone inside the perimeter is trustworthy permits attackers who penetrate the perimeter to traverse the environment unchecked. With cloud adoption and distributed workforces, relevant IT and data no longer exclusively resided within the “perimeter”.
That said, reports of this generation’s death have been greatly exaggerated. Despite the pull of modern direct-to-cloud models, on-prem network security is still supremely relevant today and demand is more durable than expected. Fortinet, which first launched with a traditional firewall product in 2002, has emerged as one of the leaders here. The company is expected to generate more than $5 billion in revenue this year, with IDC estimating that the company shipped nearly half of all firewall units in the fourth quarter of 2022. Fortinet has successfully used its foothold among its colossal install base as an on-ramp to selling adjacent networking and security solutions (e.g., SD-WAN, OT Security, etc.) to customers with hybrid networks and on-prem needs. In fact, around 30% of Fortinet’s billings last year came from government and financial services customers — industries that will forever require on-prem security and will continue refreshing their firewall deployments.
Generation II: “Lift and Shift”
As organizations began to adopt SaaS applications and cloud infrastructure, there was a shift in what needed to be secured and how that security was delivered. This generation saw the first wave of solutions delivering security through the cloud (e.g., Okta extending Active Directory into the cloud for SSO and MFA). Some leveraged the cloud to offer a 10x better platform than what was feasible before Crowdstrike aggregated data at scale in the cloud to provide superior detections, while Zscaler obviated the dependence on the traditional “hub-and-spoke” network model with its direct-to-cloud architecture. Meanwhile, vendors that initially established themselves with on-prem offerings began following their customers into the cloud, characterizing the era of “lift and shift” by developing cloud-based versions of their products (e.g., Splunk’s push to offer Splunk Cloud in 2013).
Today’s cybersecurity incumbents were founded anywhere from 10 to 30+ years ago spanning both the “on-prem” and “lift and shift” generations. For these companies, continuously adapting to the field has been key to their enduring market leadership.
Perhaps the most remarkable example of this is Palo Alto Networks. Founded in 2005, the company saw its commercial success with its next-generation firewall product (NGFW). However, by 2017 the company’s growth had slowed significantly; NGFW was an increasingly competitive market that faced headwinds from the broader shift to the cloud, and their attempts to expand into endpoint security & security analytics were ultimately lukewarm. With Nikesh Arora joining the company in 2018, the company proactively created an adaptation engine through M&A, purchasing its way to security innovation and broader cloud-focused offerings. In the last five years, Palo Alto Networks acquired 13 startups, several of which became the foundation for their “next-generation security portfolio” across Prisma Cloud (cloud security), Prisma SASE (cloud-delivered network security) and Prisma Cortex (SecOps platforms). Each of these product groups could be a standalone public company today; collectively, this portfolio is expected to generate more than $2 billion in revenue this year.
Expand
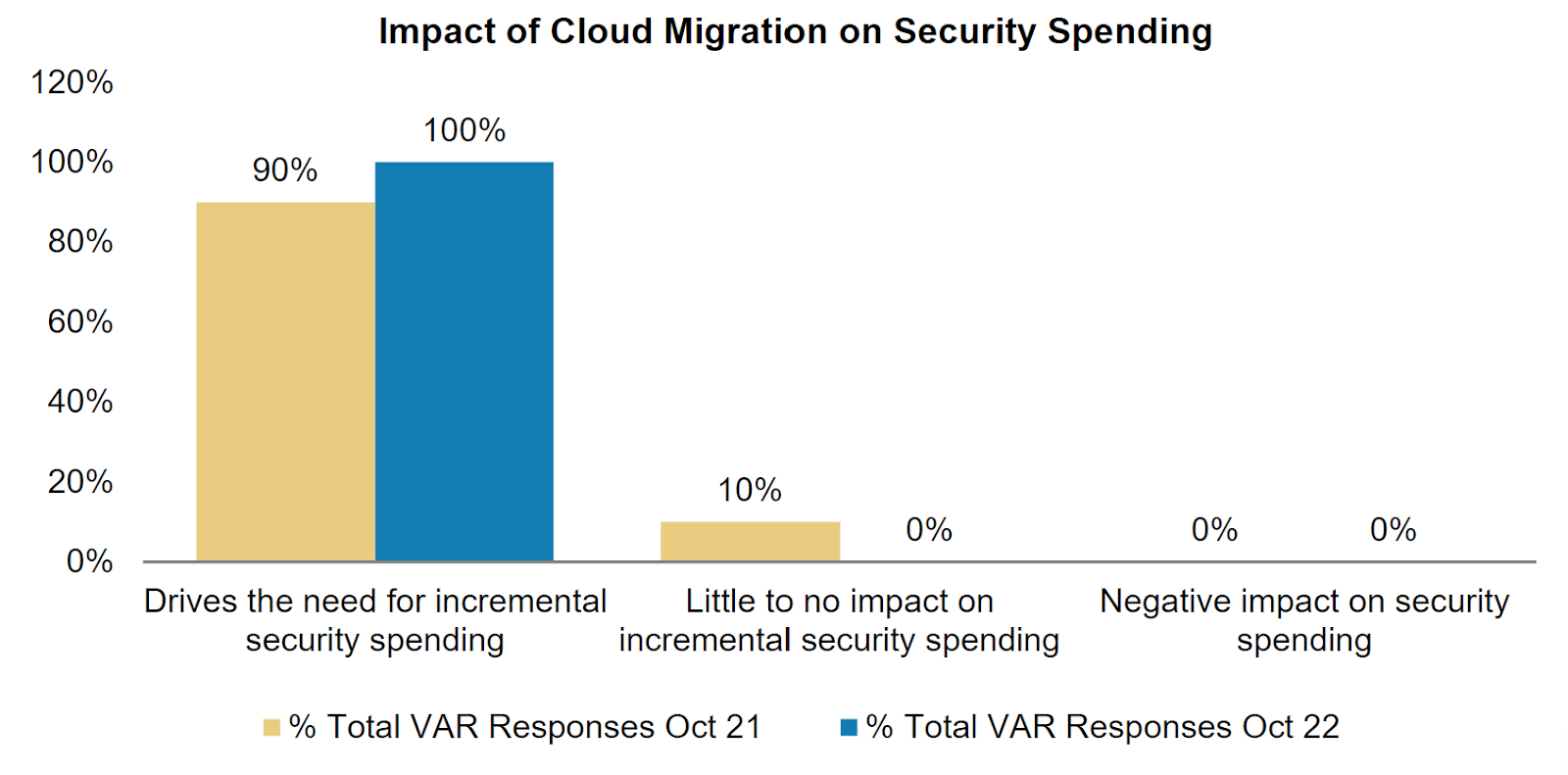
Source: Morgan Stanley, 3Q’22 VAR Survey
Generation III: “Emerging Cloud-Native”
Today’s generation of companies operates in a world in which leveraging the advantages and nuances of the cloud is table stakes. While the security ecosystem is fragmented, it is riddled with pockets of greenfield and brownfield opportunities. New attack surfaces with limited visibility abound, and vendors with superior products — whether in terms of architecture, usability, accessibility, or other features — are displacing those ill-equipped to adapt.
Several themes have begun defining today’s generation of security companies across the stack:
- Security data silos are crumbling
Emerging security models, such as Open XDR, are capitalizing on the vast amounts of security data that have historically been siloed. Given the scale and velocity of threats today, the performance and speed of security data analytics are mission-critical. The aggregation and normalization of telemetry across assets enable higher-fidelity detections in real time. New analytics models have emerged that place cloud-scale data lake houses, such as Snowflake, at their core, offering effective alternatives and extensions to traditional SIEMs for use cases centered around threat detection.
- Identity is the new center of gravity
With the decentralization of IT, new security models have flipped the script as emerging solutions treat identity as the new “perimeter” rather than any given network. Identity today extends beyond who an individual user is, instead including the devices they’re using, the context of their environment, and the bounds of their typical behavior. Naturally, identity sits center-stage across solutions built upon zero-trust principles.
- Practitioners want results, not alerts
To demonstrate quick time-to-value, security vendors often generate hundreds of alerts. However, security practitioners are inundated with more alerts than they can handle, and much of their focus is spent on triaging which alerts to prioritize rather than remediation. With this in mind, emerging vendors are focusing on minimizing false positives, prioritizing the severity of the alerts they generate, and automating their remediation to maximize results for security teams. Fully automating remediation has historically been challenging for security teams to execute at scale using prior-generation Security Orchestration, Automation, & Response (SOAR) platforms given the complexity, variability and technicality of remediation workflows. If a given security issue is not well-defined, security operations must still be in the loop — a necessity strained by the talent shortage. Next-generation automation platforms are designed with ease of use in mind, even extending accessibility to users beyond security practitioners, while other vendors have begun offering “SOAR-lite” capabilities to run automated remediation playbooks natively within their platforms.
- End-user experience is a differentiator
Cybersecurity has always faced an assumed trade-off between protection and operational agility. Historically, the efficacy of security solutions were embraced despite the pain of implementing and maintaining them. This balance has tilted as the nature of the underlying assets evolved, with more favorable approaches emerging that enable faster processes and more lightweight architectures. A key example is agentless security. With the proliferation of tools, security teams have been worn down by agent fatigue as agents require cumbersome deployments and add performance overhead. The perfect storm for agentless security emerged as trends coalesced across the shift to cloud, the standardization of cloud provider APIs, the decentralization of IT provisioning, and growing security budgets. Today, hundreds of security vendors leverage API integrations to provide broad-based visibility, identifying security issues across cloud-based applications and infrastructure without the involvement of agents. Of course, agents aren’t going away as they provide deeper real-time visibility and are still needed for active protection at runtime. However, the ease of setup and quick, non-disruptive deployments of agentless solutions have become real differentiators. With setup times measured in minutes and hours instead of days or weeks, vendors like Wiz and Orca Security have achieved unprecedented levels of adoption velocity.
Looking Ahead: 2023 and Beyond
Predicting what cybersecurity will look like in ten to twenty years would be like trying to divine the future with a Magic 8 Ball. However, a few key themes are top of mind for us:
- Security spend remains resilient but not exempt from macroeconomic headwinds
While cybersecurity is a relatively protected spend category, we anticipate enterprises will continue optimizing budgets in the face of macroeconomic uncertainty. Security teams are shifting their focus to vendors that are most mission-critical while reducing the length of contract commitments and delaying purchasing decisions. Security vendors need to continue demonstrating tangible ROI as companies heavily scrutinize potential headcount savings and risks in dollar terms.
- The tide is finally turning with vendor consolidation
With the average enterprise using over 45 different security tools, organizations still have ample opportunity to reduce costs and complexity by consolidating vendors across their security stacks. For years, broad-based consolidation has been constrained to wishful thinking as the trust that came with the efficacy of best-of-breed point solutions outweighed desires to reduce expenses or vendor relationships. Now, budget freezes and reductions are forcing functions for companies to cut down their vendor bloat and closely re-evaluate every line item. The lowest hanging fruit will be to eliminate vendor redundancies. One enterprise CISO we spoke with revealed that their organization was using Okta, CyberArk and ForgeRock across their business units, but planned to consolidate to just one of these vendors in 2023. Others will replace their point solutions with the bundled modules offered by platform vendors that are “good enough.” Companies looking to consolidate will naturally default to the gravity of mega-platforms, with Microsoft the 800-pound gorilla that will frequently be under consideration. We’re already seeing this as the average size of enterprise contracts continues to grow for vendors like Palo Alto Networks, Crowdstrike, Zscaler and Cloudflare. These platforms will also seize the opportunity to extend their capabilities through acquisitions to further fuel their growth. Meanwhile, we’re also seeing the rebundling of the security stack in the world of SMB security. Huntress is bundling managed security capabilities (endpoint security, security awareness training, etc.) on behalf of service providers serving SMBs. Meanwhile, JumpCloud, a Sapphire portfolio company, is leading the charge to unify identity, access, and device management into one platform for channel partners and SMBs.
- Existing categories will continue to be disrupted
Despite ongoing vendor consolidation and a subdued appetite for chasing down the latest security acronym, newcomers with superior products will continue displacing incumbents in areas with well-established budgets. As budget line items for those categories already exist, innovation that drives results that are better or faster by an order of magnitude will remain welcome. We’ve seen this in the past: the step change in efficacy from signature-based antivirus (AV) to behavioral-based next-gen AV and endpoint detection & response (EDR), the developer-friendly integration of static analysis into the CI/CD pipeline and the elegant plug-and-play experience of implementing agentless Cloud Security Posture Management (CSPM) vendors all enabled the disruption of incumbents. Of course, this transition never happens overnight. As discussed earlier, demand for “legacy” technologies like on-prem firewalls can be incredibly durable. But that didn’t preclude companies like Zscaler or Netskope, a Sapphire portfolio company, from taking share from existing budgets or even expanding budgets (e.g., for companies maintaining hybrid cloud environments).
- Newer security categories are primed to take off in their “second inning”
Newer security product categories are beholden to the technology adoption curve. Ultimately, trailblazers need to spend time and money evangelizing and educating their customers on their technology; as a result, it can take multiple generations before that category yields a breakout success. A great example of this is CSPM, a category pioneered by Dome9 and RedLock. While these companies found success and were acquired in 2018, in many ways they were too early as the market demand for CSPM was still forming. However, the onset of the COVID-19 pandemic lit the fuse in accelerating demand for cloud security: cloud adoption had inflected, and the idea that cloud environments needed to be secured was more widely accepted. For cloud security vendors, cloud APIs had become standardized and in-depth telemetry had become more accessible. Evangelization was the cherry on top; with mega platform brands like Palo Alto Networks acknowledging and selling cloud security solutions, enterprises can more easily justify purchases in the category today vs. five years ago. This is a pattern we see across innovation as founders try to skate toward where the puck is going. As we’ll explore in future posts, we believe a few select categories are primed to have their “second inning moment” in the coming years.
- The talent shortage isn’t going anywhere
Despite stricter budgets, recruitment and retention of security professionals remain a priority for security teams despite stricter budgets as the security talent gap persists. Security leaders will need to continue to find ways to provide team members with competitive compensation, flexible work arrangements and opportunities for long-term career development while minimizing burnout. Meanwhile, a prevention-first approach to security and selective outsourcing for triaging detection and response (e.g., managed detection & response providers like Expel, Red Canary, and Huntress Labs) can help minimize total cost of ownership while maximizing the effectiveness of an organization’s existing security talent. This is also one of the greatest opportunities where recent trends in AI will shine. We’re already seeing efforts to supercharge security operations from the likes of Microsoft with Security Copilot. Other emerging cloud-native vendors like Orca Security, Island, Endor Labs, and ARMO are leveraging foundation models to power conversational interfaces that automate workflows and generate context-rich risk insights and remediation guidance.
- The rise of security engineering
With the shift to cloud, ownership of infrastructure management began to lean out of traditional IT and into the hands of engineering. DevOps engineers emerged as a bridge between previously siloed IT operations and development teams, taking on shared responsibilities (e.g., infrastructure monitoring). Now, we’re seeing the rise of security engineers: engineers who understand the context of security and can work across DevOps, software engineering and product teams when a shift in ownership and responsibilities is warranted. Today, this organizational shift is mainly occurring within cloud-native companies, with experimental spurts among hybrid-cloud enterprises. Whether the security engineering model becomes mainstream depends on whether leaders recognize the need for security engineers in the context of their environment, navigate organizational change in re-orienting responsibilities, and land the talent they need. If great engineering & security talent are each scarce, great security engineers are like unicorns.
Cybersecurity is an industry that is only a few decades old and continues to evolve dramatically. With a bounty of challenges that power boundless innovation, we’re incredibly excited by the companies that will continue to emerge in security. If you’re a company building in security or a security practitioner, please reach out to [email protected] and [email protected].
Special thanks and shoutout to Eric Tan, Hamza Fodderwala, Prabhath Karanth, Ganesh Pai, & Joshua Tilton for reading drafts and contributing their thoughts.
Legal disclaimer
Disclaimer: Nothing presented within this article is intended to constitute investment advice, and under no circumstances should any information provided herein be used or considered as an offer to sell or a solicitation of an offer to buy an interest in any investment fund managed by Sapphire Ventures (“Sapphire”). Information provided reflects Sapphires’ views as of a time, whereby such views are subject to change at any point and Sapphire shall not be obligated to provide notice of any change. Companies mentioned in this article are a representative sample of portfolio companies in which Sapphire has invested in which the author believes such companies fit the objective criteria stated in commentary, which do not reflect all investments made by Sapphire. A complete alphabetical list of Sapphire’s investments made by its direct growth and sports investing strategies is available here. No assumptions should be made that investments listed above were or will be profitable. Due to various risks and uncertainties, actual events, results or the actual experience may differ materially from those reflected or contemplated in these statements. Nothing contained in this article may be relied upon as a guarantee or assurance as to the future success of any particular company. Past performance is not indicative of future results.